U.S. Immigration and Customs Enforcement, known as ICE, is gearing up to take access of, aka hack, more smartphones. In 2017 ICE paid $2.2 million to Cellebrite. Now according to a federal filing ICE will contract with Cellebrite for between $30 and $35 million.
Cellebrite is an Israeli company known to most people for its 2016 offer to hack the San Bernardino shooter’s iPhone for the FBI. According to reports, that is exactly what the company did, something the FBI denies. No matter what happened in that case, Cellebrite builds tools to bypass smartphone security, download data and reportedly inject spyware.

The (up to) $35 million is according to the filing earmarked for “universal forensic extraction devices (UFED)” and “accessories licenses, training and support services.” for one year, with an option to extend for up to five years. The Daily Beast contacted Officer Tracy Riley of ICE for details and Riley said she would “absolutely” not provide more details about the contract.
While it’s not clear how ICE uses Cellebrite’s technology. It’s cause for concern given the history of warrantless searches of phones by Customs and Border Protection. If you think being a U.S. citizen is protection from that, you are wrong.
Cellebrite has worked with Myanmar to search the phones of two journalists jailed by that government. After a hack revealing some data (900gb) from the company’s end user license management system Vice confirmed the company has also sold UFEDs to Russia, the United Arab Emirates, and Turkey and a 2016 press release on Cellebrite’s own website boast they have “40,000 UFED licenses in 100 countries[…]” — So, by anyone’s count of countries on earth, Cellebrite has sold to over half of them.
The company has also bragged about the ability to hack nearly every iPhone on the market. I’m taking note of this, because China (a nation Reuters says Cellebrite has sold to) recently used a zero day vulnerability in iOS to spy on Uyghurs, a people group the nation has been putting in forced labor camps. China was also known to inject spyware into devices at the border.
It’s not just iPhones. Cellebrite’s capabilities are far reaching. The company’s UFED is advertised (publicly on the website) as being able to unlock any device running iOS 7 to iOS 12.3, and Android smartphones including the most recent Samsung Galaxy models, and the company says it will soon support devices from Huawei, LG, Motorola, and Xiaomi.
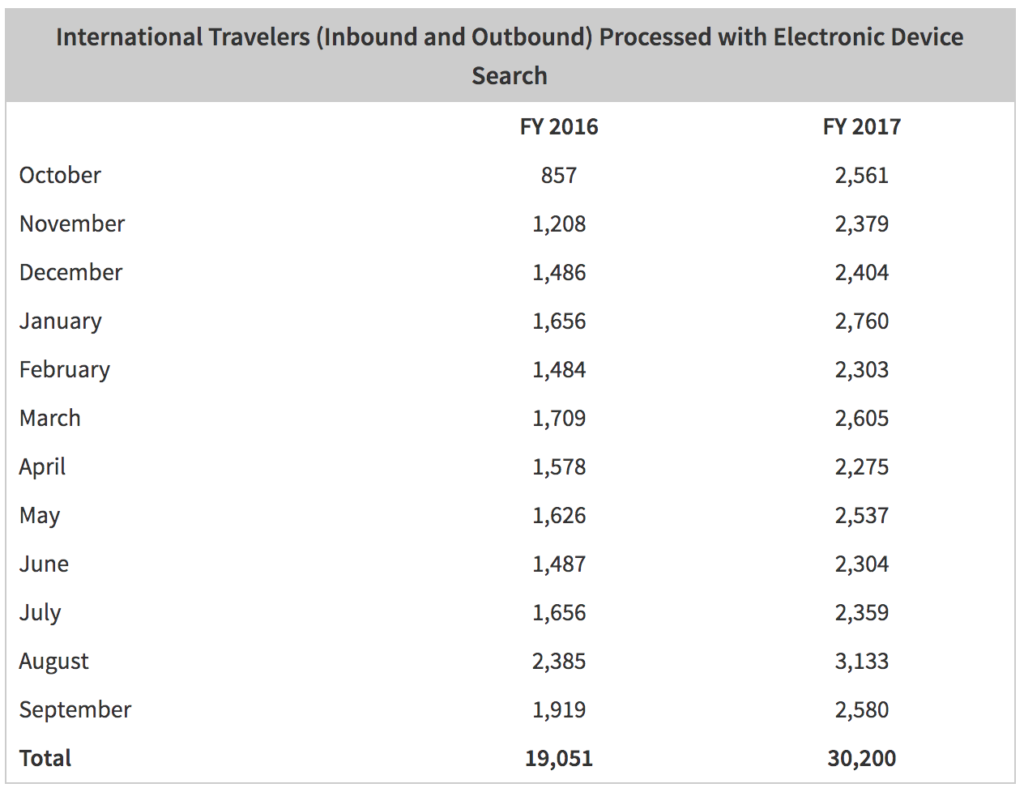
Forbes, two years ago reported that the Cellebrite devices can cost between $5,000 and $15,000. With a government spend of up to $35 million, that means a lot of potential devices capable of searching a lot more devices, in the hands of people who have searched a lot of devices. According to data from 2017, CBP searched 30,200 devices at the border, for both inbound and outbound travellers, this is a big increase from 2016. We don’t yet have, and probably never will have 2018 data.
We also learned earlier this year that Homeland Security was spying on journalists, activists, and immigration lawyers and recommending them for enhanced screenings and device searches by the CBP. The Border Patrol attempted to explain the profiles of 59 journalists, lawyers, and activists first by claiming they were necessary to secure the border, and later saying all 59 people in the documents leaked to NBC 7 by DHS were present in November, 2018 when violence “broke out at the border”.
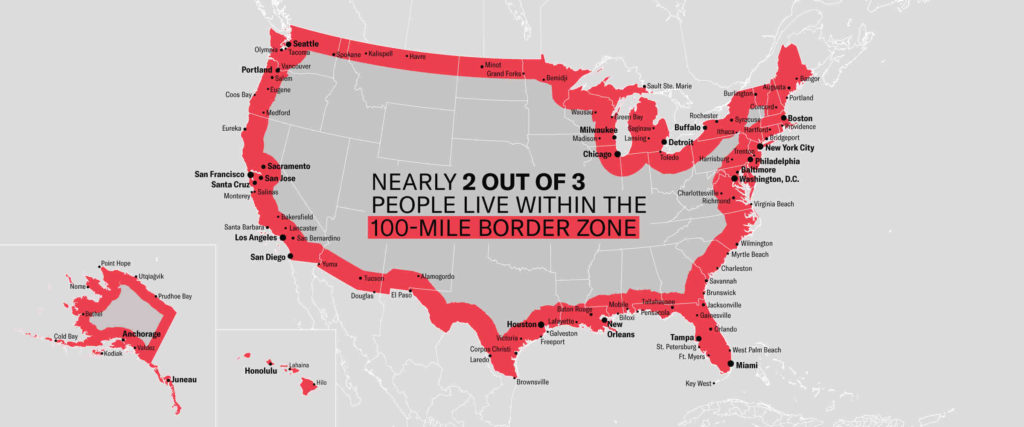
These Federal agencies do not need warrants to search at ports of entry. U.S. Customs and Border Protection specifically has authority to operate within 100 miles of any U.S. “external boundary.” This means Border Patrol agents, can operate immigration checkpoints at any place in the U.S. within 100 miles of a border. With approximately 65% of the U.S. population living within 100 miles of a border, this new move by ICE has the potential to impact a lot of people.
H/t Aric Toler – Header Image by jonathan mcintosh
Mason Pelt, is a guest author for Internet News Flash. He’s been a staff writer for SiliconANGLE and has written for TechCrunch, VentureBeat, Social Media Today and more.
He’s a Managing Director of Push ROI, and he acted as an informal adviser when building the first Internet News Flash website. Ask him why you shouldn’t work with Spring Free EV.

Comments are closed, but trackbacks and pingbacks are open.